Help Center
Enter your Login ID & Password to access SSC portal.
User ID : Employee Pay sheet number is your User ID.
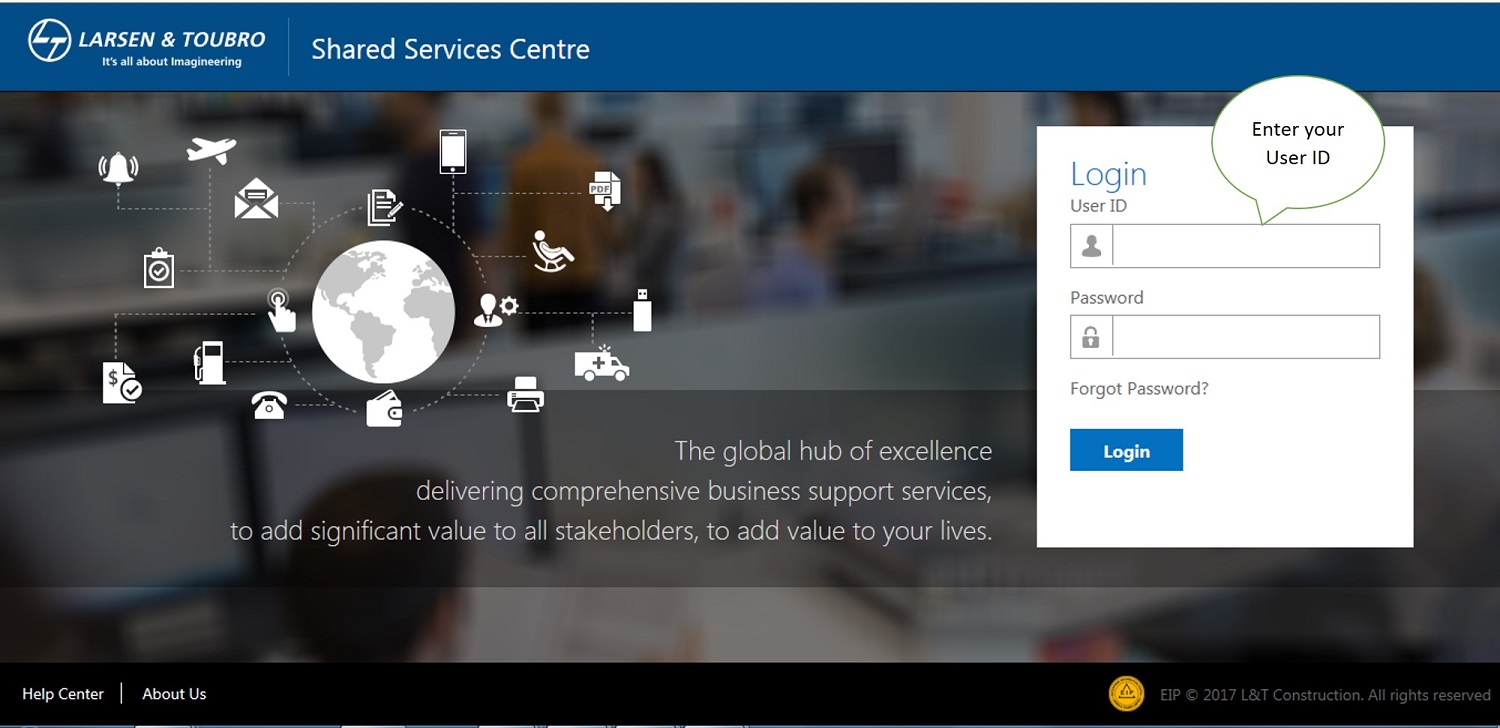
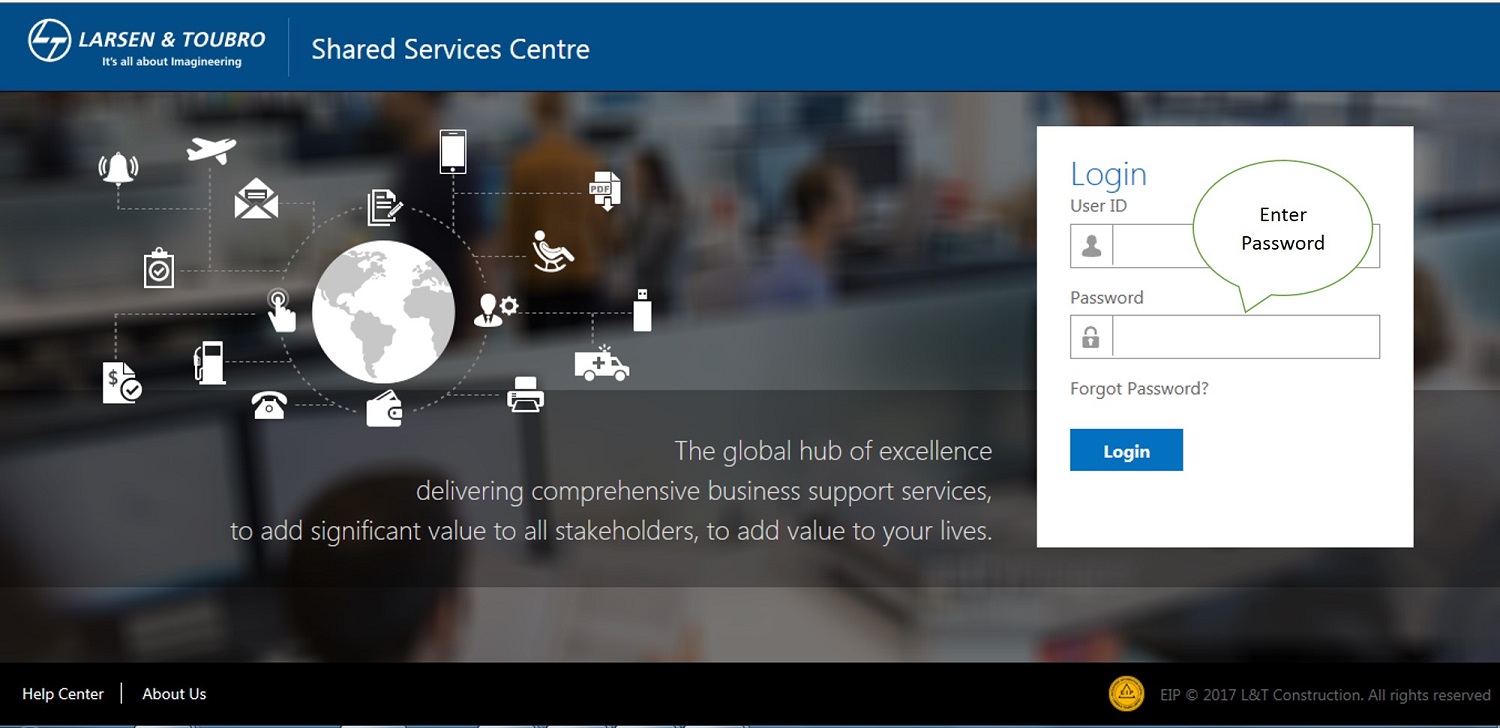
Password: The Default password for first time login user is “DATE OF BIRTH” in Format DDMMYYYY, Example If Date of Birth is 29/12/2014 then your password will be 29122014.
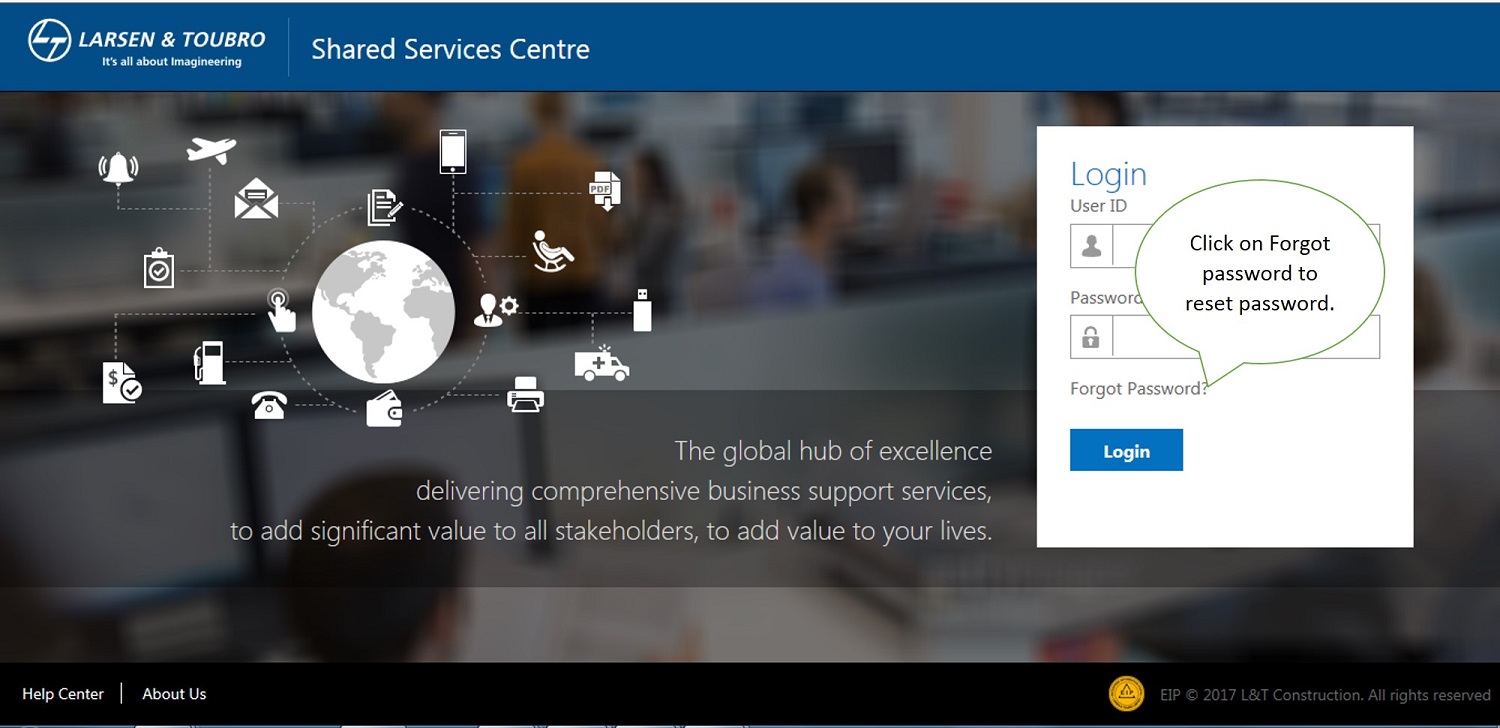
Forgot Password/ OTP SMS - One Time Password SMS:
Option for Forgot Password can be opted in case of Password Locked or forgotten. In order to strengthen the security and confidentiality, OTP (One time password through SMS from registered Mobile number) facility is introduced.
If Mobile number is not available in Master Data of SSC Portal, the system will not allow the user to change password, since OTP cannot be sent to his/her registered mobile. In such cases User may contact HR / SSC to update Mobile No. in the Payroll System.
Enter user ID & CAPTCHA.
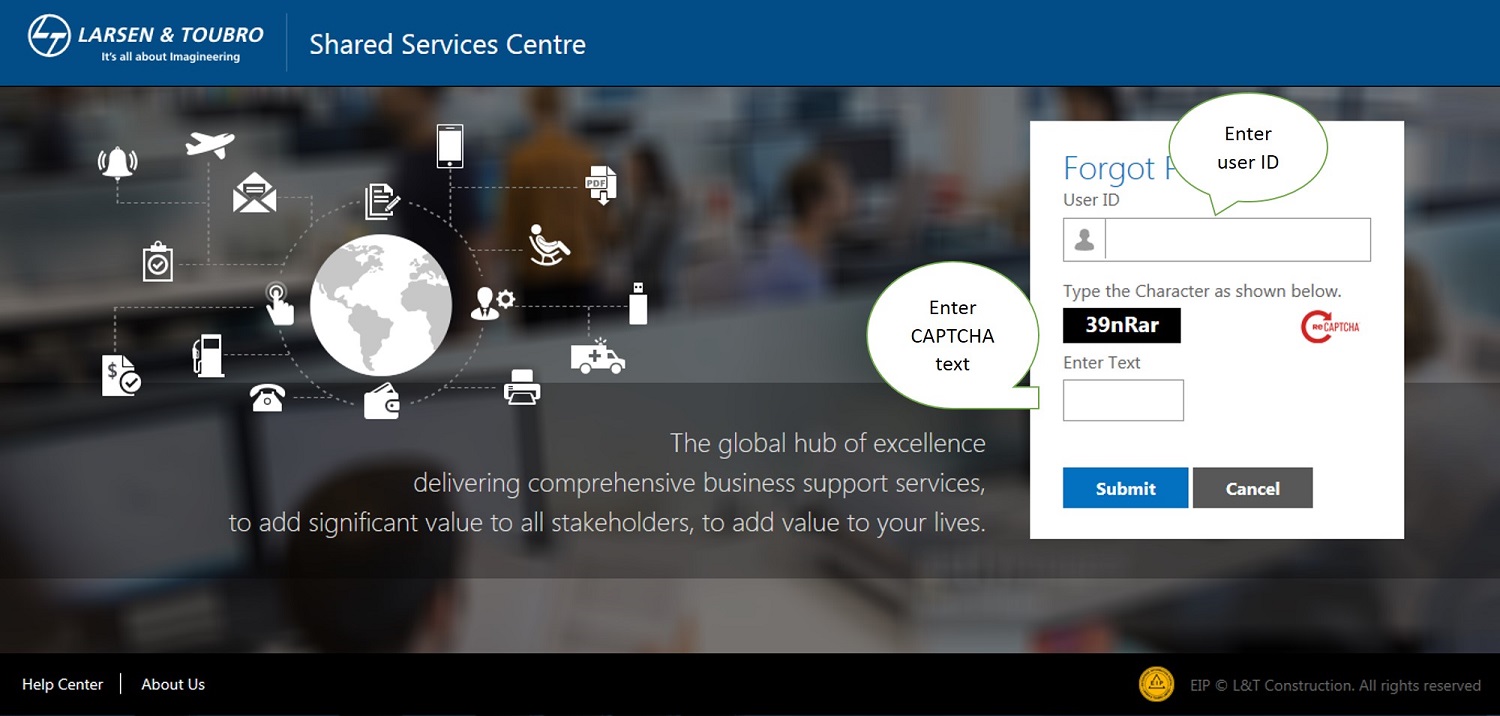
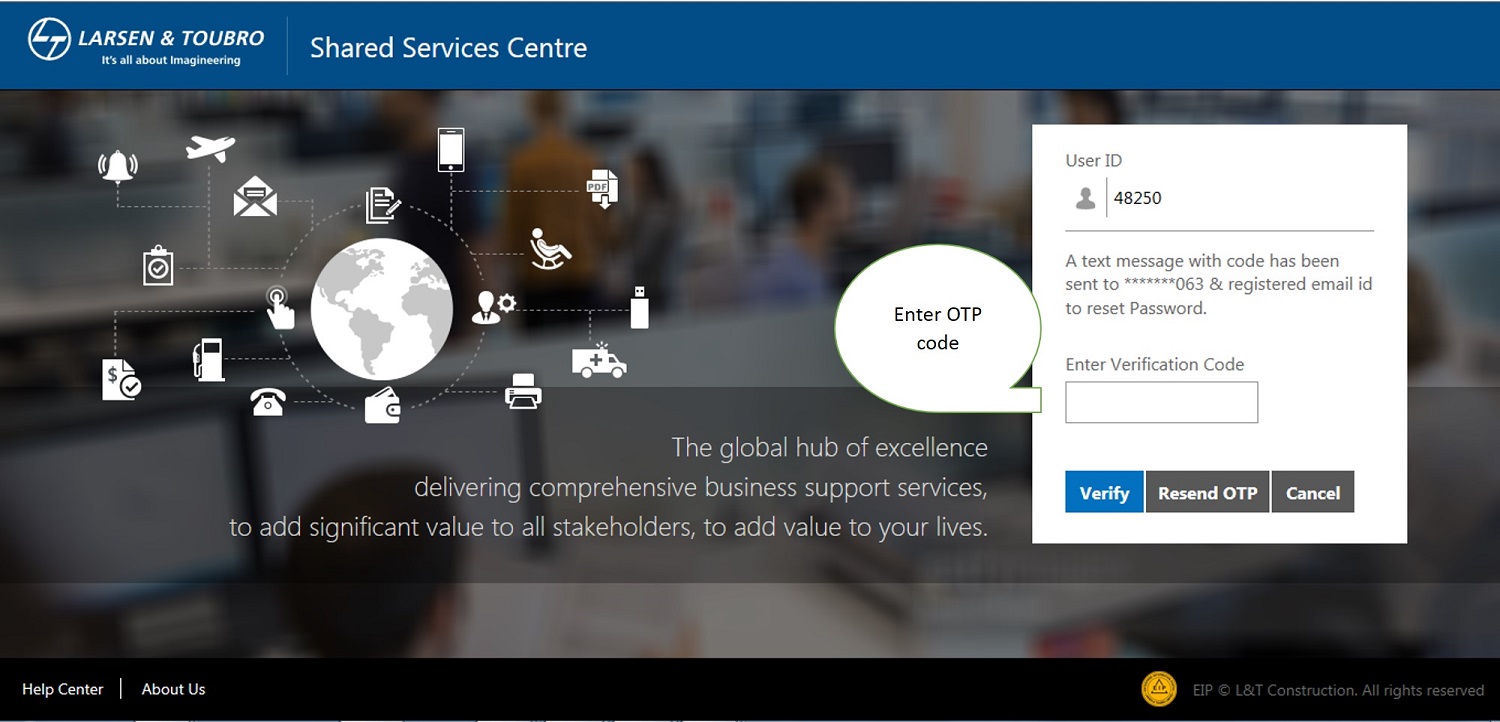
Enter OTP code as received on your register mobile number.
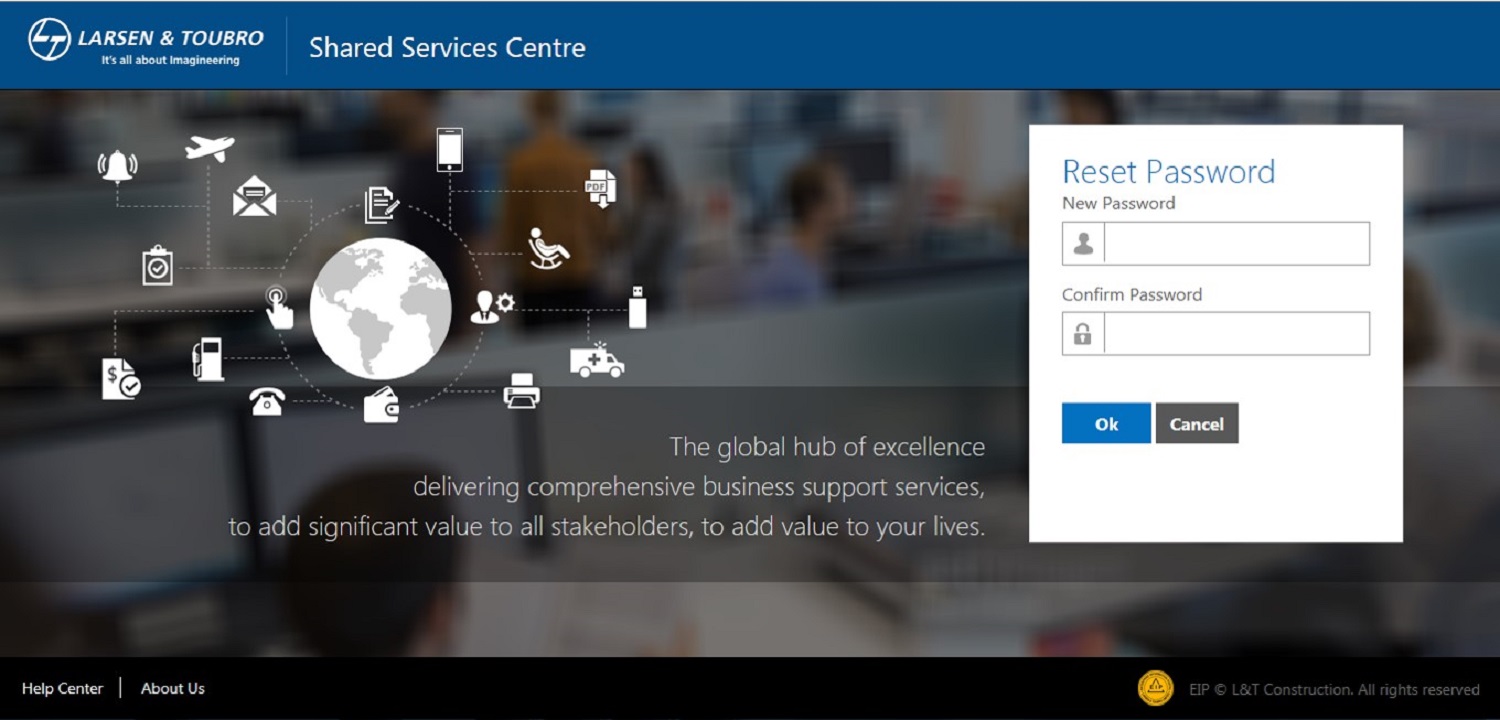
Enter your New Password.
1.0 Overview
Password, being an important aspect of computer security, forms the basic level of protection of user accounts. A poorly chosen password may result in compromise of L&T's entire corporate network and data. All L&T employees (including contractors, vendors etc.) with access to systems are responsible for taking appropriate measures, as outlined below, to select and secure their systems by having strong and complex passwords.
2.0 Purpose
The purpose of this policy is to establish a standard for creation of strong user-level & system-level password, its protection, frequency of change and guidelines for use within L&T’s network. All desktops, servers, systems, applications and network devices are to be protected by strong and complex passwords.
3.0 Scope
This policy applies to every individual accessing L&T’s resources at any time at any location. All employees, contractors and vendors of L&T have to comply with the policy.
4.0 Password creation guidelines
Password should be a strong and complex password. Some of the guidelines for setting a strong complex password are as below. It should
- Contain both upper and lower case characters (e.g., a-z, A-Z).
- Have letters as well as alphanumeric characters (e.g., 0-9, @#).
- Not contain first name/last name and/or dictionary words or any combination of these.
The use of control characters and other non-printing characters is not allowed or permitted because they may inadvertently cause network transmission problems or unintentionally invoke certain system utilities.
Random password generators shall be considered for usage to generate complex passwords
5.0 Password Policy for Applications
This section addresses password policy for all applications which are in production or in development phase. Departments and data owners are accountable for ensuring proper controls are in place during the lifecycle of an application, including the design, development, testing, production, and maintenance. Application developers are responsible for implementing the password policy mentioned below.
- The passwords for servers must be atleast eight (8) characters long and be different from last five (5) passwords.
- User Passwords for all applications are to be changed every 70 days
- User can have option of max five(5) unsuccessful login attempts
- User can have max of 3 simultaneous sessions.
In circumstances where compliance with the Password Policy is not supported by some applications or databases, then the responsibility lies with the system or application administrator to have strong complex passwords and adhere to password protection standards for the machine where the application is installed.
6.0 Password Protection Standards
Passwords should not be stored in readable form in batch files, automatic logon scripts, software macros, terminal function keys, in computers without access control, or in other locations where unauthorized persons might discover or use them.
Passwords should always be encrypted when held in storage for any specific reason or when transmitted over networks. This will prevent them from being sniffed using clear text sniffers. If there is a business requirement to transmit a password through email then the user id and encrypted password should be sent in a separate email.
The display and printing of passwords must be masked or obscured so that unauthorized parties are not able to observe or subsequently recover them.
- No passwords are to be spoken, written, shared, hinted at or in any way known to anyone other than the user involved.
- No passwords are to be revealed on questionnaires/security forms or to co-workers while on a vacation. In case it’s required then a temporary account has to be created by the OD IT for the resources to be accessed.
- No employee is permitted to use any feature of a system or an application to “remember” a password on any computer.
Payroll description will be available here. Payroll description will be available here. Payroll description will be available here. Payroll description will be available here.
EBC description will be available here. Payroll description will be available here. Payroll description will be available here. Payroll description will be available here.
RBS description will be available here. Payroll description will be available here. Payroll description will be available here. Payroll description will be available here.
TEMS description will be available here. Payroll description will be available here. Payroll description will be available here. Payroll description will be available here.
i-TEMS description will be available here. Payroll description will be available here. Payroll description will be available here. Payroll description will be available here.

